Short anti-spam and anti-virus information page
Spam
The word "spam" is used on the internet to refer to unsolicited email often
promoting pornographic websites, get-rich-quick schemes, or goods you can
buy.
For some it is a real nuisance, they are getting many of these emails
a day, some get hardly any. Here are some tips on what you may be able
to do about it:
-
Be careful with your email address, you don't hand out your telephone number
to just anybody either, do you? One idea is to have more than one email
address, the "main" one that you hand out to friends, business associates
etc., and then another one that you use when for example a website requires
that you enter an email address to download files.
-
It is not uncommon to include the email address when creating a homepage
on the internet. The following bit of HTML code makes it possible to click
on a link and the email program of the user will open up with the "To:"
field ready to send an email: <a href="mailto:send_me_spam@spam.org">email
address</a>. Well, there are programs that the spammers can use to search
for this HTML code and gather email addresses with. So including your email
address like that will almost certainly mean that you eventually end up
receiving spam.
-
Spam email often tells you to reply to a certain email address if you do
not want to receive email from that particular spammer anymore. Don't,
that way the spammer knows that he/she has hit a real human email address.
The same goes with retaliating against the spammer. It is not worth the
effort. Often, the email address that the spam email seems to be sent from
doesn't even exist, or it belongs to somebody else who has no fault in
the spam being sent to you.
-
This brings me to my last "tip". As already written, the email address
that the spam was sent from often doesn't exist at all. Email servers are
usually capable of performing what is called a "reverse DNS lookup" when
receiving an email. This does increase the work done by the email server,
but it also means that the email server will reject an email from an address
that doesn't exist. If you are using an ordinary ISP email account, speak
(or write) to the ISP about getting them to do this, if they can't or won't,
choose a different ISP.
Chain letters
These are related to spam, but they are sent out, sometimes by people who
want to make a buck, sometimes as a joke. They then get sent on by people
who obviously don't properly read the email and think about the content.
Have you heard the story about the guy who invented chess? I'm not relating
it correctly, but you'll get the idea. A king thought this was such a great
invention that he offered the inventor anything he wanted that sounded
reasonable. So the inventor asked for 1 grain of rice to be put on the
first square of the chess board, twice that number on the second square,
twice that number again on the third square. Doesn't sound like a lot,
does it? Well, a chess board has 64 squares, on the last square the will
be 9.22337E+18 grains of rice. The story goes on to tell that the inventor
was beheaded by the king. Examples of chainletters that I have received
were:
-
I should forward a copy of the received email to 10 other people. I should
add my address and within a few weeks I would receive, free of charge,
Erricsons brand new mobile phone, yeah right. With the speed of email and
with the above story in mind, that would probably bankrupt Erricson.
-
Microsoft and Walt Disney were collaborating on an email tracking program,
all I had to do was to forward the email to 10 other people and I would
receive $1000 (I think it was). Well, even if true, would I like Microsoft
to have an email tracking program that tracks emails no matter where they
are sent from or to?
-
A variation of the above email was only going to give me a small amount
of money per user that I sent the email to, but I would also receive money
for emails sent by those that I had sent the email to. I received the email
in the month of March when apparently it was still going strong despite
the fact that the email stated that one would only receive money for email
sent before January.
-
False virus warnings are often sent by well-meaning people as well.
Viruses and Trojan Horses
This bit will primarily be relevant to users of Intel based PC's running
Windows, and with one exception (that I'll get to) is the truth about these
nasties.
-
You don't want them (I guess you knew that)!
-
There is usually no need to be paranoid about them.
-
They can't appear out of nowhere, and they can't get inside your PC by
themselves. YOU (yes, you) have to do something that gets them inside your
PC.
So how can they get inside your computer:
-
You can access a file which either is a trojan horse, or contains a virus,
on a floppy diskette or ZIP disk or CD-ROM.
-
You can access a file which either is a trojan horse, or contains a virus,
that came from the internet.
Access is a very important word here. The mere presence of a nasty file
on your harddisk, floppy, CD-ROM or in an email sent to you does not mean
that you have to whip out that recent backup you have ready (you do have
a backup, don't you?).
A trojan horse has to be available as executable code. In "the old days"
that meant that only files with the extensions .EXE or .COM could be trojan
horses or contain virusses. But now we also have things such as "Visual
Basic Scripts" (.VBS) and Word or Excel macros. But whatever form they
appear under, they have to exist as CODE, not just mere data.
And when YOU decide to run the code that contains the trojan horse
or virus, you get bitten. Not before.
Lets look at a brief list of extensions used for different kinds of
code:
| COM |
Typically used by some MS-DOS programs |
| EXE |
Used by MS-DOS and Windows programs |
| VBS |
Visual Basic Script |
| JS |
JavaScript |
So how do you run code?
-
You doubleclick on a program icon in Windows Explorer.
-
Within your email program you doubleclick on an attached file.
Doubleclicking a program icon
Again, a program is a file with any of the above mentioned extensions.
To be more "friendly" Windows usually hides the extensions of files on
your harddisk. If you want to be able to see the extensions of files in
Explorer (in Windows 98), choose "View -> Folder Options" and you will
be presented with an option that says it all. Click on this link to see
a screenshot of what it should look like.
Doubleclicking on an attached file within an email
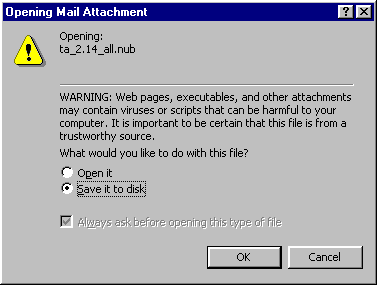 When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.
When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.
 When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.
When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.
 When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.
When
I doubleclick on an attached file sent to me by email, I see this. That
is not yet dangerous. Saving it to disk is not dangereous. Selecting "Open
it" and clicking OK is. If it is a
virus, it may now be time to restore that backup of mine.